4725 : A user account was disabled
Generates each time a computer or a user object is disabled
For user accounts, event is stored on domain controllers, member servers or workstations
For computer accounts, event is stored on domain controllers only
Monitoring Recommendations :
Monitor for potential suspicious activities, abuse of privileges.
Monitor if you have domain accounts or local accounts that should never been disabled or for which you need to monitor every change
If you have critical assets, servers or workstation, monitor local accounts (SAM accounts)
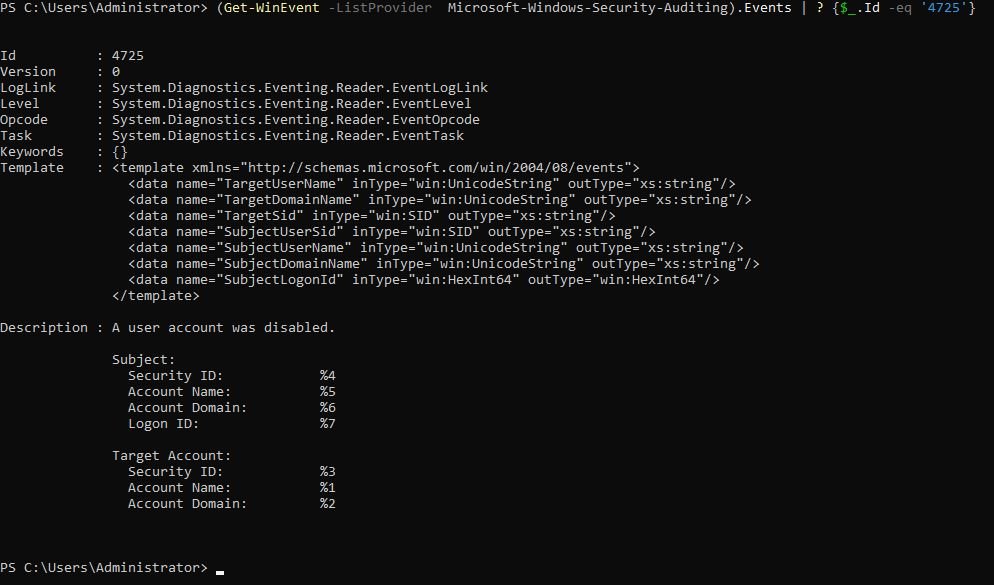
Get event details with PowerShell :
PS C:\Users\Administrator> (Get-WinEvent -ListProvider Microsoft-Windows-Security-Auditing).Events | ? {$_.Id -eq '4725'}
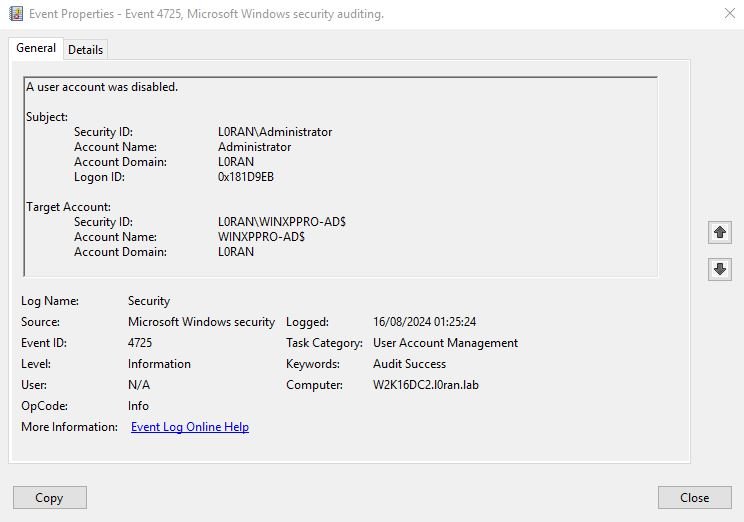
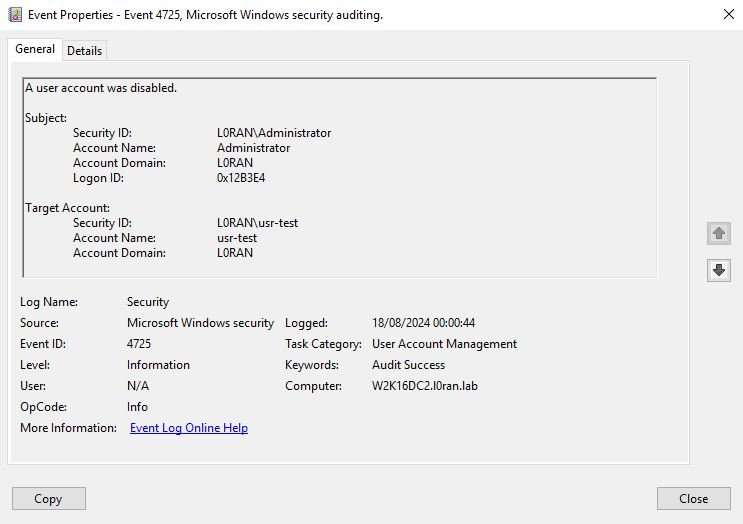
Exemples of 4725 events
Exemple of disabled computer account event
Exemple of disabled user account event
Retreive and export in CSV all Events ID 4725 for the current domain
Powershell script to retreive in a CSV file all logged Events ID 4725 for the current domain.
# Audit 4725 Events (a user account was disabled) & export events information to CSV table