4624 : An account was successfully logged on
- Generates when a logon session is created (on destination machine). It generates on the computer that was accessed, where the session was created.
| 4624 | An account was successfully logged on |
| Category | Audit Logon/Logoff |
| Event Type | Success |
| Provider | Microsoft-Windows-Security-Auditing |
| Channel | Security |
| Criticity | Low |
| Volumetry | HIGH |
| Reference | https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-4624 |
Monitoring Recommendations :
- Always consider monitoring 4624 event, because it’s very talkative and reports useful information.
- Because this event is typically triggered by the SYSTEM account, it’s recommend to report it only whenever “Subject\Security ID” isn’t SYSTEM
- Use filters when polling domain controller for this event because it’s one of the most noisiest event.
Security Monitoring Recommendations :
- Monitor “Restricted Admin” mode. monitor logons by “New Logon\Security ID” in relation to “Logon Type“=10 and “Restricted Admin Mode“=”Yes”. If “Restricted Admin Mode“=”No” for these accounts, trigger an alert.
- Monitor all logon events for accounts with administrator privileges, monitor this event with “Elevated Token“=”Yes”.
- Monitor all logon events for MSa and GMSa service accounts, monitor for events with “Virtual Account“=”Yes”.
- Monitor for a mismatch between the logon type and the account that uses it (for example, if Logon Type 4-Batch or 5-Service is used by a member of a domain administrative group), monitor Logon Type in this event.
- If you monitor for potentially malicious software, or software that isn’t authorized to request logon actions, monitor this event for Process Name.
- If you have a trusted logon processes list, monitor for a Logon Process that isn’t from the list.
- Monitor Logon Restrictions :
- If the user account “New Logon\Security ID” should never be used to log on from the specific Computer:.
- If New Logon\Security ID credentials shouldn’t be used from Workstation Name or Source Network Address.
- If a specific account, such as a service account, should only be used from your internal IP address list (or some other list of IP addresses). In this case, you can monitor for Network Information\Source Network Address and compare the network address with your list of IP addresses.
- Monitor NTLM Usage :
- If a particular version of NTLM is always used in your organization. In this case, you can use this event to monitor Package Name (NTLM only), for example, to find events where Package Name (NTLM only) doesn’t equal NTLM V2.
- If NTLM isn’t used in your organization, or shouldn’t be used by a specific account (New Logon\Security ID). In this case, monitor for all events where Authentication Package is NTLM.
- If the Authentication Package is NTLM. In this case, monitor for Key Length not equal to 128, because all Windows operating systems starting with Windows 2000 support 128-bit Key Length.
Exemples of 4624 events
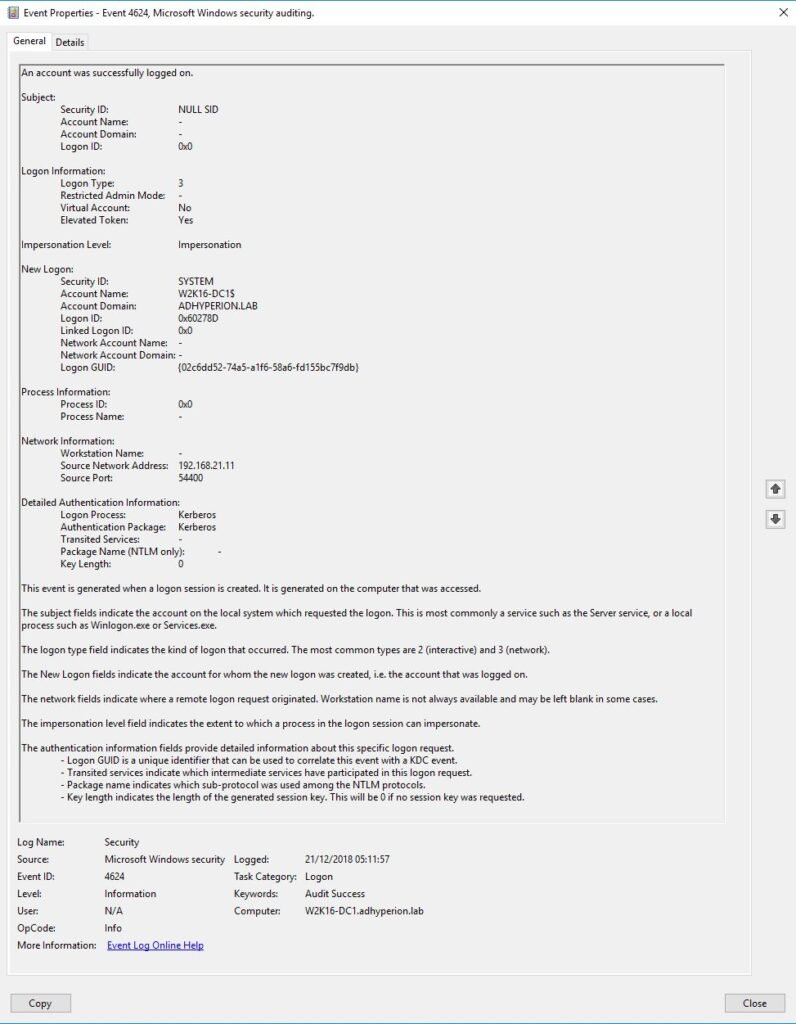
Get 4624 event details with PowerShell :
- Event 4624 Structure (Version 2)
| Displayed Value | XML Value | Description |
|---|---|---|
| [Subject] Security ID | SubjectUserSid | SID of account or Name (if SID can’t be resolved) that reported information about successful logon or invokes it. |
| [Subject] Account Name | SubjectUserName | Name of the account that reported information about successful logon |
| [Subject] Account Domain | SubjectDomainName | Subject’s domain or computer name. For some well-known security principals, such as LOCAL SERVICE or ANONYMOUS LOGON, the value of this field is “NT AUTHORITY“. |
| [Subject] Logon ID | SubjectLogonId | Hexadecimal value that can be correlated with recent events that might contain the same Logon ID, for example, “4672: Special privileges assigned to new logon.“ |
| [Logon Information] Logon Type | Logon Type | The type of logon that happened. The next table contains the list of possible values for this field |
| [Logon Information] Restricted Admin Mode | Restricted Admin Mode | Only populated for RemoteInteractive logon type sessions1. This value is a Yes/No flag indicating if the credentials provided were passed using Restricted Admin mode. If not a RemoteInteractive logon, then this value is the string: – |
| [Logon Information] Virtual Account | Virtual Account | A “Yes” or “No” flag, which indicates if the account is a virtual account (for example, “Managed Service Account“), which was introduced in Windows 7 and Windows Server 2008 R2 to identify the account that a given Service uses, instead of just using “NetworkService“. |
| [Logon Information] Elevated Token | Elevated Token | A “Yes” or “No” flag. If “Yes”, then the session this event represents is elevated and has administrator privileges. – %%1842 value stands for YES – %%1843 value stands for NO |
| [Impersonation Level] Impersonation Level | Impersonation Level | Can have one of these four values: – SecurityAnonymous2 (displayed as empty string) – SecurityIdentification3 (displayed as “Identification“) – SecurityImpersonation4 (displayed as “Impersonation“) – SecurityDelegation5 (displayed as “Delegation“) |
| [New Logon] Security ID | Security ID | SID of the account or Name (if SID can’t be resolved) for which logon was performed. |
| [New Logon] Account Name | Account Name | Name of the account for which logon was performed. |
| [New Logon] Account Domain | Account Domain | Subject’s domain or computer name. For some well-known security principals, such as LOCAL SERVICE or ANONYMOUS LOGON, the value of this field is “NT AUTHORITY“. |
| [New Logon] Logon ID | Logon ID | Hexadecimal value that can be correlated with recent events that might contain the same Logon ID, for example, “4672: Special privileges assigned to new logon.“ |
| [New Logon] Linked Logon ID | Linked Logon ID | Hexadecimal value of the paired logon session. If there’s no other logon session associated with this logon session, then the value is “0x0“. |
| [New Logon] Network Account Name | Network Account Name | User name that’s used for outbound (network) connections. Valid only for NewCredentials logon type. If not NewCredentials logon, then this value will be the string: – |
| [New Logon] Network Account Domain | Network Account Domain | Domain for the user that’s used for outbound (network) connections. Valid only for NewCredentials logon type. If not NewCredentials logon, then this value will be the string: – |
| [New Logon] Logon GUID | Logon GUID | GUID that can be correlated with another event that can contain the same Logon GUID, “4769: A Kerberos service ticket was requested event on a domain controller” and “4648: A logon was attempted using explicit credentials” and “4964: Special groups have been assigned to a new logon“. |
| [Process Information] Process ID | Process ID | Hexadecimal Process ID of the process that attempted the logon. Once converted the hexadecimal value to decimal, it can be compares to the values in Task Manager. This process ID with a process ID in other events, for example, “4688: A new process has been created” Process Information\New Process ID. |
| [Process Information] Process Name | Process Name | Full path and the name of the executable for the process |
| [Network Information]6 Workstation Name | Workstation Name | Machine name from which a logon attempt was performed. Network logons with Kerberos have no workstation information. |
| [Network Information] Source Network Address | Source Network Address | IP address of machine from which logon attempt was performed. NTLM logons have no TCP/IP details. |
| [Network Information] Source Port | Source Port | The source port that was used for logon attempt from remote machine. 0 for interactive logons. NTLM logons have no TCP/IP details. |
| [Detailed Authentication Information] Logon Process | Logon Process | Name of the trusted logon process that was used for the logon. See event “4611: A trusted logon process has been registered with the Local Security Authority” description for more information. |
| [Detailed Authentication Information] Authentication Package | Authentication Package | Name of the authentication package that was used for the logon authentication process. Default packages loaded on LSA startup are located in “HKLM\SYSTEM\CurrentControlSet\Control\Lsa\OSConfig” registry key. Other packages can be loaded at runtime. When a new package is loaded a “4610: An authentication package has been loaded by the Local Security Authority” (typically for NTLM) or “4622: A security package has been loaded by the Local Security Authority” (typically for Kerberos) event is logged to indicate that a new package has been loaded along with the package name. The most common authentication packages are: NTLM, Kerberos, Negociate8 |
| [Detailed Authentication Information] Transited Services | Transited Services | List of transmitted services. Transmitted services are populated if the logon was a result of a S4U9 (Service For User) logon process. |
| [Detailed Authentication Information] Package Name (NTLM only) | Package Name (NTLM only) | Name of the LAN Manager subpackage that was used during logon. Possible values are: “LM”, “NTLM V1”, “NTLM V2”. Only populated if “Authentication Package” = “NTLM”. |
| [Detailed Authentication Information] Key Length | Key Length | Length of NTLM Session Security key. Typically it has 128-bit or 56-bit length. This parameter is always 0 if “Authentication Package” = “Kerberos” (not applicable for Kerberos protocol), and also has a 0 value if Kerberos was negotiated using Negotiate authentication package. |
- Netlogon Types
| Logon Type | Logon Type Name | Description |
|---|---|---|
| 0 | System | Used only by the System account, for example at system startup. |
| 2 | Interactive | A user logged on to this computer. |
| 3 | Network | A user or computer logged on to this computer from the network. |
| 4 | Batch | Batch logon type is used by batch servers, where processes can be run on behalf of a user without their direct intervention. |
| 5 | Service | The Service Control Manager started a service. |
| 7 | Unlock | This workstation was unlocked. |
| 8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials don’t traverse the network in plaintext (also called cleartext). |
| 9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections. |
| 10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
| 11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller wasn’t contacted to verify the credentials. |
| 12 | CachedRemoteInteractive | Same as RemoteInteractive. This type is used for internal auditing. |
| 13 | CachedUnlock | Workstation logon. |
- Security Provider List
| Code | Name | Description |
|---|---|---|
| Negotiate | C:\Windows\system32\lsasrv.dll | Negotiate between Kerberos and NTLM. |
| NegoExtender | C:\Windows\system32\negoexts.DLL | Extension to negotiate with additional SSPs. |
| Kerberos | C:\Windows\system32\kerberos.DLL | Kerberos v5 implementation. |
| NTLM | C:\Windows\system32\msv1_0.DLL | NTLM implementation |
| TSSSP | C:\Windows\system32\tspkg.DLL | Implements CredSSP (SSO for TerminalServices & RDP). |
| pku2u | C:\Windows\system32\pku2u.DLL | Implements P2P authentication (e.g. homegroups). |
| CloudAP | C:\Windows\system32\cloudAP.DLL | Implements Azure cloud authentication. |
| WDigest | C:\Windows\system32\wdigest.DLL | Implements digest authentication (HTTP, LDAP, …). |
| Schannel | C:\Windows\system32\schannel.DLL | Implements TLS (including SSL & PCT which are considered obsolete). |
| Microsoft Unified Security Protocol Provider | C:\Windows\system32\schannel.DLL |
- Get XML template of the 4624 event
(Get-WinEvent -ListProvider Microsoft-Windows-Security-Auditing).Events | ? {$_.Id -eq '4624'}
- Script to export in a CSV filtered 4624 events
- Filter events by : Last 24H, NTLMv1,for specific user
# Audit 4624 Events (An account was successfully logged on)
# EventID_4624_AccountLoggedOnSuccessfully.ps1
# wiki.l0ran.xyz
# September 5th, 2024
# Filter out all 4624 Events (Use it carefully because 4624 is a very noisy event)
$Xpath_4624_all = '*[System[EventID=4624]]'
# Filter out all last 24H events 4624
$Xpath_4624_all_Last24h = "Event[System[(EventID=4624) and TimeCreated[timediff(@SystemTime) <= 86400000]]]"
# Filter NTLM V1
$Xpath_4624_NTLMv1 = "Event[System[(EventID=4624)]]and Event[EventData[Data[@Name='LmPackageName']='NTLM V1']]"
# Filter on specific user
$xpath_4624_SpecificUsr = "Event[System[(EventID=4624)]]and Event[EventData[Data[@TargetUserName='username']]]"
# CSV Output folder
$CSVOutputFolder = 'C:\tmp'
# CSV Outfile
$CSVOutFile = "$CSVOutputFolder\EventID_4624_AccountLoggedOnSuccessfully.csv"
$dom = @()
$DCList = @()
$dom = (Get-ADDomainController).domain
$DCList = (Get-ADDomainController -filter * -server $dom).hostname
function get-4624
{param
([Object]
[Parameter(Mandatory=$true, ValueFromPipeline=$true, HelpMessage="Data to process")]
$InputObject
)
process
{$eventXml_4624 = ([xml]$InputObject.ToXml()).Event
[PSCustomObject]@{
Date = [DateTime]$eventXml_4624.System.TimeCreated.SystemTime
RecordID = $eventXml_4624.System.EventRecordID
Computer = $eventXml_4624.System.Computer
Provider = $eventXml_4624.System.Provider.Name
Level = $eventXml_4624.System.Level
EventID = $eventXml_4624.System.EventID
EventVersion = $eventXml_4624.System.Version
Keywords = $eventXml_4624.System.Keywords
SubjectUserSid = $eventXml_4624.EventData.data[0].'#text'
SubjectUserName = $eventXml_4624.EventData.data[1].'#text'
SubjectDomainName = $eventXml_4624.EventData.data[2].'#text'
SubjectLogonId = $eventXml_4624.EventData.data[3].'#text'
TargetUserSid = $eventXml_4624.EventData.data[4].'#text'
TargetUserName = $eventXml_4624.EventData.data[5].'#text'
TargetDomainName = $eventXml_4624.EventData.data[6].'#text'
TargetLogonId = $eventXml_4624.EventData.data[7].'#text'
LogonType = $eventXml_4624.EventData.data[8].'#text'
LogonProcessName = $eventXml_4624.EventData.data[9].'#text'
AuthenticationPackageName = $eventXml_4624.EventData.data[10].'#text'
WorkstationName = $eventXml_4624.EventData.data[11].'#text'
LogonGuid = $eventXml_4624.EventData.data[12].'#text'
TransmittedServices = $eventXml_4624.EventData.data[13].'#text'
LmPackageName = $eventXml_4624.EventData.data[14].'#text'
KeyLength = $eventXml_4624.EventData.data[15].'#text'
ProcessId = $eventXml_4624.EventData.data[16].'#text'
ProcessName = $eventXml_4624.EventData.data[17].'#text'
IpAddress = $eventXml_4624.EventData.data[18].'#text'
IpPort = $eventXml_4624.EventData.data[19].'#text'
ImpersonationLevel = $eventXml_4624.EventData.data[20].'#text'
RestrictedAdminMode = $eventXml_4624.EventData.data[21].'#text'
TargetOutboundUserName = $eventXml_4624.EventData.data[22].'#text'
TargetOutboundDomainName = $eventXml_4624.EventData.data[23].'#text'
VirtualAccount = $eventXml_4624.EventData.data[24].'#text'
TargetLinkedLogonId = $eventXml_4624.EventData.data[25].'#text'
ElevatedToken = $eventXml_4624.EventData.data[26].'#text'}}
}
foreach ($DC in $DCList)
{write-host "Working on $DC" -ForegroundColor Cyan
Get-WinEvent -Logname security -ComputerName $DC -FilterXPath $Xpath_4624_NTLMv1 -ea 0 |
get-4624 |
Export-Csv -Delimiter ';' -path $CSVOutFile -NoTypeInformation -Append}
# Remove duplicates records (if so)
$FilteredCSV = import-csv -Path $CSVOutFile -Delimiter ";"
$FilteredCSV = ((($FilteredCSV) | Sort-Object -Property RecordID -Unique) | Sort-Object -Descending -Property Date) |
Export-Csv -Delimiter ";" -path $CSVOutFile -NoTypeInformation
- Restricted Admin Mode [Version 2] [Type = UnicodeString]: Only populated for RemoteInteractive logon type sessions. This value is a Yes/No flag indicating if the credentials provided were passed using Restricted Admin mode. Restricted Admin mode was added in Windows 8.1 and Windows Server 2012 R2, but this flag was added to the event in Windows 10.
Reference: https://blogs.technet.com/b/kfalde/archive/2013/08/14/restricted-admin-mode-for-rdp-in-windows-8-1-2012-r2.aspx. ↩︎ - SecurityAnonymous (displayed as empty string): The server process can’t obtain identification information about the client, and it can’t impersonate the client. It’s defined with no value given, and thus, by ANSI C rules, defaults to a value of zero. ↩︎
- SecurityIdentification (displayed as “Identification“): The server process can obtain information about the client, such as security identifiers and privileges, but it can’t impersonate the client. This value is useful for servers that export their own objects, for example, database products that export tables and views. Using the retrieved client-security information, the server can make access-validation decisions without being able to use other services that are using the client’s security context. ↩︎
- SecurityImpersonation (displayed as “Impersonation“): The server process can impersonate the client’s security context on its local system. The server can’t impersonate the client on remote systems. This type is the most common. ↩︎
- SecurityDelegation (displayed as “Delegation“): The server process can impersonate the client’s security context on remote systems. ↩︎
- The fields for IP address/port and workstation name are populated depending on the authentication context and protocol used. LSASS will audit the information the authenticating service shares with LSASS. For example, network logons with Kerberos likely have no workstation information, and NTLM logons have no TCP/IP details. ↩︎
- The Negotiate security package selects between Kerberos and NTLM protocols. Negotiate selects Kerberos unless it can’t be used by one of the systems involved in the authentication or the calling application didn’t provide sufficient information to use Kerberos. ↩︎
- S4U is a Microsoft extension to the Kerberos Protocol to allow an application service to obtain a Kerberos service ticket on behalf of a user – most commonly done by a front-end website to access an internal resource on behalf of a user. For more information about S4U, see https://msdn.microsoft.com/library/cc246072.aspx ↩︎
