4726 : A user account was deleted
- Generates every time user object was deleted
- Event is stored on domain controllers, member servers or workstations
| Event ID | 4726 |
| Title | A user account was deleted |
| Category | User Account Management |
| Event Type | Success |
| Provider | Microsoft-Windows-Security-Auditing |
| Channel | Security |
| Criticity | Low |
| Volumetry | Low |
| Reference | https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-4726 |
Monitoring Recommendations :
- Monitor domain or local account (SAM accounts) that should never be deleted (VIPs, high-privileged or service accounts)
- Monitor critical assets, servers or workstation, monitor local accounts (SAM accounts)
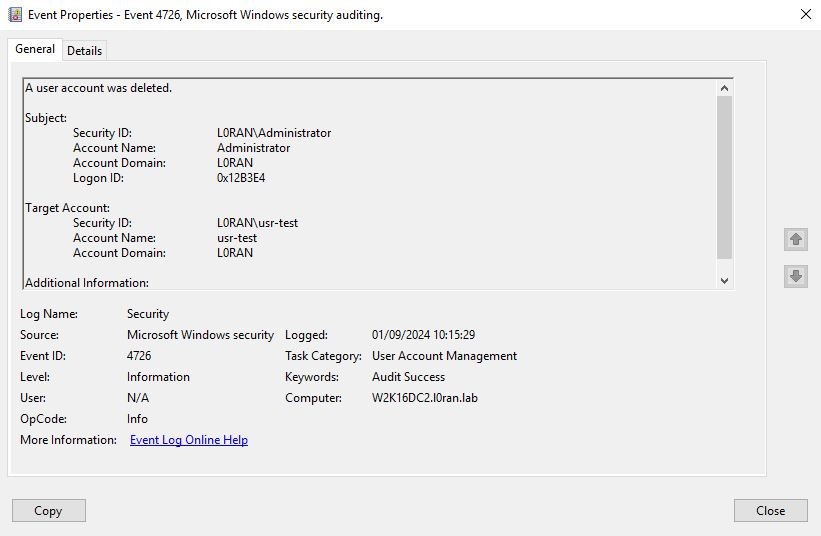
Exemples of 4726 events
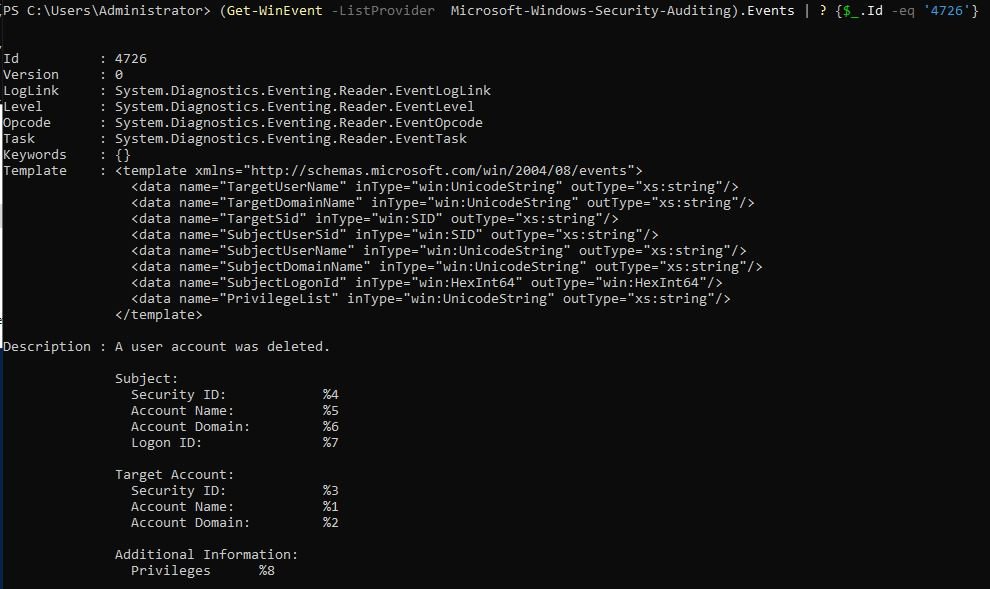
Get event details with PowerShell :
- Event Structure
| Displayed Value | XML Value | Description |
|---|---|---|
| [Target Account] Account Name | TargetUserName | Name of the deleted account. |
| [Target Account] Account Domain | TargetDomainName | Domain or computer name of the deleted account. |
| [Target Account] Security ID | TargetSid | SID of the deleted account.. The SID is resolved when possible and if not, displayed in it’s original format. |
| [Subject] Security ID | SubjectUserSid | SID of account that deleted the account. The SID is resolved when possible and if not, displayed in it’s original format. |
| [Subject] Account Name | SubjectUserName | Name of the account that requested the “delete user account” operation |
| [Subject] Account Domain | SubjectDomainName | Domain or computer name of the account that deleted the account. |
| [Subject] Logon ID | SubjectLogonId | Value that can help to correlate this event with recent events that might contain the same Logon ID, for example, “4624: An account was successfully logged on.” |
| [Additional Information] Privileges | PrivilegeList | List of user privileges which were used during the operation, for example, SeBackupPrivilege. This parameter might not be captured in the event, and in that case appears as “-” |
- Get XML template of the event
PS C:\Users\Administrator> (Get-WinEvent -ListProvider Microsoft-Windows-Security-Auditing).Events | ? {$_.Id -eq '4726'}
- Powershell script to retreive in a CSV file all logged Events ID 4726 for the current domain.
# Audit 4726 Events (a user account was deleted) & export events information to CSV table
# EventID_4726_UserAccountWasDeleted.ps1
# wiki.l0ran.xyz
# August 30th, 2024
# $Xpath24h = '*[System[(EventID=4726) and TimeCreated[timediff(@SystemTime) <= 86400000]]]'
$filterxpath = '*[System[EventID=4726]]'
# CSV Output folder
$CSVOutputFolder = 'C:\tmp'
# CSV Outfile
$CSVOutFile = "$CSVOutputFolder\EventID_4726_UserAccountWasDeleted.csv"
$dom = @()
$DCList = @()
$dom = (Get-ADDomainController).domain
$DCList = (Get-ADDomainController -filter * -server $dom).hostname
function get-4726
{param
( [Object]
[Parameter(Mandatory=$true, ValueFromPipeline=$true, HelpMessage="Data to process")]
$Event
)
process
{$eventXml_4726 = ([xml]$Event.ToXml()).Event
[PSCustomObject]@{
Date = [DateTime]$eventXml_4726.System.TimeCreated.SystemTime
RecordID = $eventXml_4726.System.EventRecordID
Computer = $eventXml_4726.System.Computer
Provider = $eventXml_4726.System.Provider.Name
Level = $eventXml_4726.System.Level
EventID = $eventXml_4726.System.EventID
Keywords = $eventXml_4726.System.Keywords
TargetUserName = $eventXml_4726.EventData.data[0].'#text'
TargetDomainName = $eventXml_4726.EventData.data[1].'#text'
TargetSid = $eventXml_4726.EventData.data[2].'#text'
SubjectUserSid = $eventXml_4726.EventData.data[3].'#text'
SubjectUserName = $eventXml_4726.EventData.data[4].'#text'
SubjectDomainName = $eventXml_4726.EventData.data[5].'#text'
SubjectLogonId = $eventXml_4726.EventData.data[6].'#text'
PrivilegeList = $eventXml_4726.EventData.data[7].'#text'}}
} # End function get-4726
foreach ($DC in $DCList)
{write-host "Working on $DC" -ForegroundColor Cyan
Get-WinEvent -Logname security -ComputerName $DC -FilterXPath $filterxpath -ea 0 |
get-4726 |
Export-Csv -Delimiter ';' -path $CSVOutFile -NoTypeInformation -Append}
