4776 : The computer attempted to validate the credentials for an account
- Generates every time that a credential validation occurs using NTLM authentication
- Occurs only on the computer that is authoritative for the provided credentials, domain controller for domain accounts and member servers or workstations for local accounts
- Logs both successful and unsuccessful credential validation attempts
- Also generates when a workstation unlock event occurs
- Does not generate when a domain account logs on locally to a domain controller
| 4776 | The computer attempted to validate the credentials for an account |
| Category | Audit Credential Validation |
| Event Type | Success, Error |
| Provider | Microsoft-Windows-Security-Auditing |
| Channel | Security |
| Criticity | Low |
| Volumetry | Medium |
| Reference | https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-4776 |
Monitoring Recommendations :
- It shows only the computer name (Source Workstation) from which the authentication attempt was performed
- By watching this event on domain controllers you can see all NTLM authentication attempts for domain accounts
- For monitoring local account logon attempts, it’s better to use event “4624: An account was successfully logged on” because it contains more details and is more informative
Security Monitoring Recommendations :
- Can be an indicator of Account Takeover attempts, or Brute Force Passwords attacks
- Monitor if NTLM authentication shouldn’t be used for a specific account
- Monitor if a local account should be used only locally (for example, network logon or terminal services logon isn’t allowed), monitor all events where Source Workstation and Computer (where the event was generated and the credentials are stored) have different values.
- If you want to collect all NTLM authentication attempts in the domain, or on a local machine
- Keep focus on high-privileged and service accounts
| What to track ? | Error Code | Description |
|---|---|---|
| User logon with misspelled or bad user account | 0xC0000064 0xC000006D | Account Enumeration – N events in the last N minutes can be an indicator of an attack |
| User logon with misspelled or bad password | 0xC000006A 0xC000006D | Brute Force Attack – N events in the last N minutes can be an indicator of an attack |
| User logon with account locked | 0xC0000234 | Brute Force Attack – Monitor for critical accounts |
| User logon outside authorized hours | 0xC000006F | Account Compromised – Monitor for critical accounts |
| User logon from unauthorized workstation | 0xC0000070 | Account Compromised – Monitor for critical accounts |
| User logon to account disabled by administrator | 0xC0000072 | Account Compromised – N events in the last N minutes can be an indicator of an account compromise |
| User logon with expired account | 0xC0000193 | Account Compromised – Monitor for critical accounts |
| LAN Manager Authentication Level mismatch | 0xC000006D | Configuration Error – Review LAN Manager authenticatiion Level between source and target |
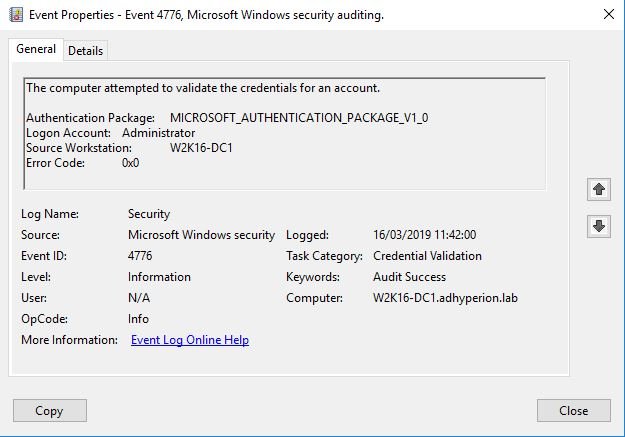
Exemples of 4776 events
Get 4776 event details with PowerShell :
- Event 4776 Structure
| Displayed Value | XML Value | Description |
|---|---|---|
| Authentication Package1 | PackageName | For this event it’s always “MICROSOFT_AUTHENTICATION_PACKAGE_V1_0“ |
| Logon Account | TargetUserName | Name of the account that had its credentials validated by the Authentication Package |
| Source Workstation | Workstation | Name of the computer from which the logon attempt originated |
| Error Code | Status | Contains error code for Failure events. For Success events this parameter has “0x0“ |
- The table below contains most common error codes for this event
| Error Code | Error Status | Description |
|---|---|---|
| 0x0 | STATUS_SUCCESS | No errors |
| 0xC0000022 | STATUS_ACCESS_DENIED | The root cause may be various. |
| 0xC000005E | STATUS_NO_LOGON_SERVERS | No logon servers available to service the logon request. |
| 0xC0000064 | STATUS_NO_SUCH_USER | The username you typed does not exist. Bad username. |
| 0xC000006A | STATUS_WRONG_PASSWORD | Account logon with misspelled or bad password. |
| 0xC000006D | STATUS_LOGON_FAILURE | – Generic logon failure. Some of the potential causes for this: – An invalid username and/or password was used – LAN Manager Authentication Level mismatch between the source and target computers. |
| 0xC000006E | STATUS_ACCOUNT_RESTRICTION | Account logon with restricted account (blank password usage and not allowed, policy restrictions). |
| 0xC000006F | STATUS_INVALID_LOGON_HOURS | Account logon outside authorized hours. |
| 0xC0000070 | STATUS_INVALID_WORKSTATION | Account logon from unauthorized workstation. |
| 0xC0000071 | STATUS_PASSWORD_EXPIRED | Account logon with expired password. |
| 0xC0000072 | STATUS_ACCOUNT_DISABLE | Account logon to account disabled by administrator. |
| 0xC000009A | STATUS_INSUFFICIENT_RESSOURCES | Ressource issue on system that prevents Netlogon to operate properly. |
| 0xC00000DC | STATUS_INVALID_SERVER_STATE | The SAM or the LSA was in the wrong state to perform the operation. DC is shutting down or restarting. |
| 0xC000018A | STATUS_NO_TRUST_LSA_SECRET | Connection to the domain is broken from the computer user is trying to log on to. |
| 0xC0000192 | STATUS_NETLOGON_NOT_STARTED | The netlogon service was not started. |
| 0xC0000193 | STATUS_ACCOUNT_EXPIRED | Account logon with expired account. |
| 0xC0000199 | STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT | Computer account used instead of user account. May happen when “Allow local system to use computer identity for NTLM” is confiured, and when the owner of the WAA group is expired, or when the computer failed to join a domain. |
| 0xC0000224 | STATUS_PASSWORD_MUST_CHANGE | Account logon with “Change Password at Next Logon” flagged. |
| 0xC0000234 | STATUS_ACCOUNT_LOCKED_OUT | Account logon with account locked. |
| 0xC00002EE | STATUS_UNFINISHED_CONTEXT_DELETED | Security context deleted before the context was completed. |
| 0xC0000371 | STATUS_NO_SECRET | The local account store does not contain secret material for the specified account. |
| 0xC0000413 | STATUS_AUTHENTICATION_FIREWALL_FAILED | The computer you are loggin to is protected by a firewall, and the specified account is not allowed to authenticate. |
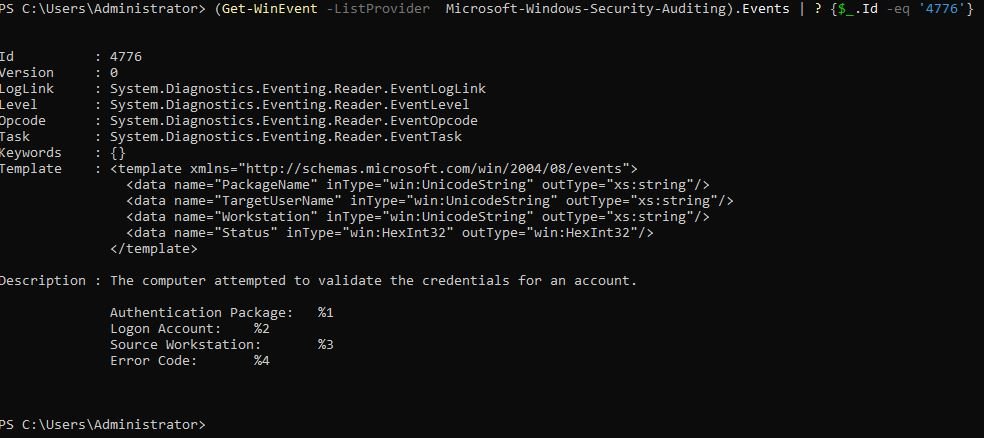
- Get XML template of the 4776 event
(Get-WinEvent -ListProvider Microsoft-Windows-Security-Auditing).Events | ? {$_.Id -eq '4776'}
- Powershell script to export in a CSV file all 4776 events containing error codes for the current domain.
# Audit 4776 Events (the computer attempted to validate the credentials for an account)
# EventID_4776_ComputerAttemptedToValidateCredentialForUser(NTLMv1).ps1
# wiki.l0ran.xyz
# September 5th, 2024
# Audit 4776 Events with error code != 0x0
$filterxpath = "*[System[(EventID=4776)]] and *[EventData[Data[@Name='Status']!='0x0']]"
# CSV Output folder
$CSVOutputFolder = 'C:\tmp'
# CSV Outfile
$CSVOutFile = "$CSVOutputFolder\EventID_4776_NTLMv1-CredentialsValidated.csv"
$dom = @()
$DCList = @()
$dom = (Get-ADDomainController).domain
$DCList = (Get-ADDomainController -filter * -server $dom).hostname
function get-4776
{param
( [Object]
[Parameter(Mandatory=$true, ValueFromPipeline=$true, HelpMessage="Data to process")]
$Event
)
process
{$eventXml_4776 = ([xml]$Event.ToXml()).Event
[PSCustomObject]@{
Date = [DateTime]$eventXml_4776.System.TimeCreated.SystemTime
RecordID = $eventXml_4776.System.EventRecordID
Computer = $eventXml_4776.System.Computer
Provider = $eventXml_4776.System.Provider.Name
Level = $eventXml_4776.System.Level
EventID = $eventXml_4776.System.EventID
Keywords = $eventXml_4776.System.Keywords
PackageName = $eventXml_4776.EventData.data[0].'#text'
TargetUserName = $eventXml_4776.EventData.data[1].'#text'
Workstation = $eventXml_4776.EventData.data[2].'#text'
Status = $eventXml_4776.EventData.data[3].'#text'}}
} # End function get-4776
foreach ($DC in $DCList)
{write-host "Working on $DC" -ForegroundColor Cyan
Get-WinEvent -Logname security -ComputerName $DC -FilterXPath $filterxpath -ea 0 |
get-4776 |
Export-Csv -Delimiter ';' -path $CSVOutFile -NoTypeInformation -Append}
# Remove duplicates records (if so)
$FilteredCSV = import-csv -Path $CSVOutFile -Delimiter ";"
$FilteredCSV = ((($FilteredCSV) | Sort-Object -Property RecordID -Unique) | Sort-Object -Descending -Property Date) |
Export-Csv -Delimiter ";" -path $CSVOutFile -NoTypeInformation
- Note Authentication package is a DLL that encapsulates the authentication logic used to determine whether to permit a user to log on. Local Security Authority (LSA) authenticates a user logon by sending the request to an authentication package. The authentication package then examines the logon information and either authenticates or rejects the user logon attempt. ↩︎
